Cybersecurity Consideration in Operational Technology
Cybersecurity Considerations in Operational Technology¶
Operational Technology (OT) environments increasingly depend on embedded devices, typically running Linux or Android, to perform control, monitoring, and supervisory functions. As these systems become more connected and remotely manageable, the security of firmware, bootloaders, and embedded software supply chains becomes inseparable from OT security itself. Modern threats demonstrate that weaknesses in update mechanisms, package integrity, or firmware provenance can directly lead to industrial disruption.
Historically, OT environments relied on system isolation, proprietary protocols, and infrequent updates. Today, however, modern OT integrates connected embedded Linux/Android controllers, remote management interfaces, OTA update mechanisms, third‑party software supply chains, and virtualized or containerized workloads.
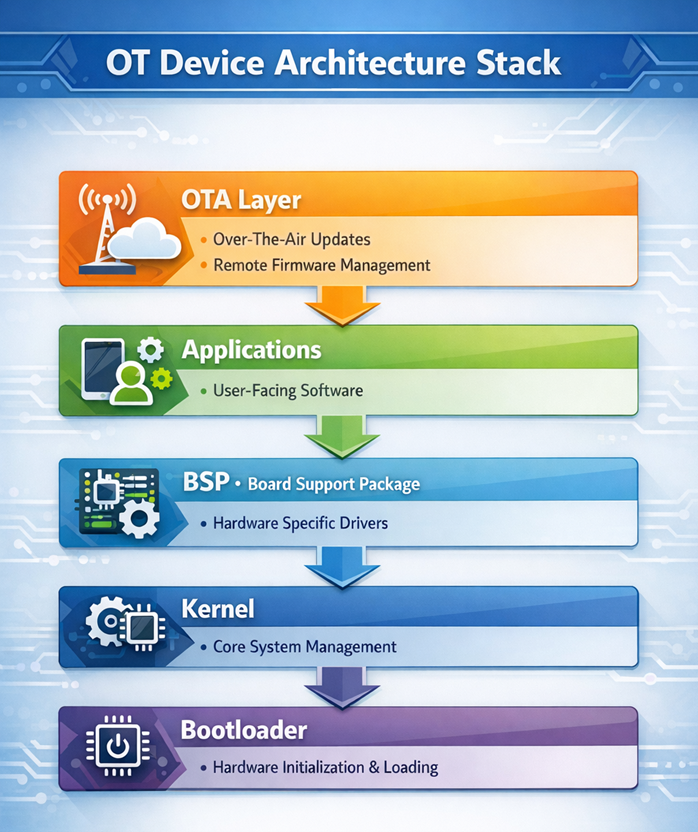
As industrial systems become increasingly interconnected, the attack surface now extends far beyond traditional control networks. What was once confined to the factory floor has expanded into the firmware supply chain itself, encompassing third‑party hardware, embedded software stacks, bootloaders, update servers, and remote maintenance channels. This shift means vulnerabilities can be introduced long before a device is deployed in the field. The integrity of PLCs, RTUs, drives, smart sensors, and safety‑critical controllers now depends as much on secure development and supply‑chain assurance as on perimeter defenses.
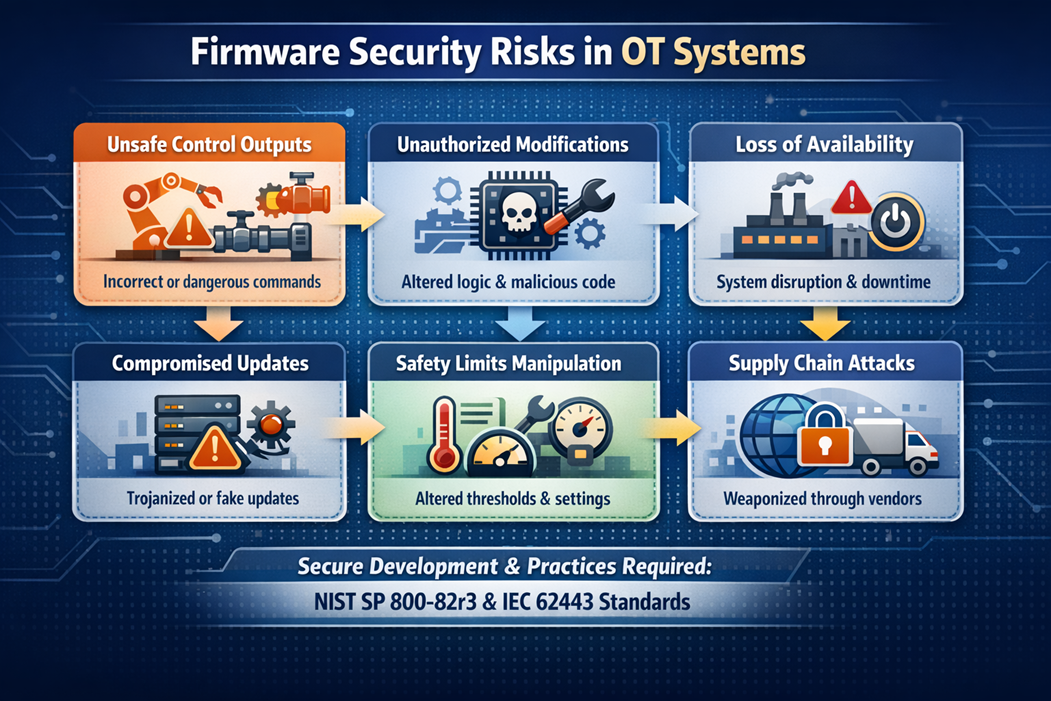
Breakdowns in embedded security practices can produce cascading operational and safety impacts, including:
![]() Unsafe Control Outputs
Unsafe Control Outputs
If firmware integrity is compromised, controllers may issue incorrect or dangerous commands, opening valves beyond limits, mispositioning robotics, altering setpoints, or manipulating actuator timing. Many OT devices lack runtime integrity checks or output validation, allowing corrupted logic to directly affect the physical world.
![]() Unauthorized System Modification
Unauthorized System Modification
Weak authentication, insecure boot processes, or unsigned updates allow attackers to alter device behavior without detection. This may include modifying ladder logic, injecting malicious routines, or reconfiguring safety interlocks. Unauthorized changes can persist across reboots and evade monitoring tools that assume trusted firmware.
![]() Loss of Availability or Physical Process Disruption
Loss of Availability or Physical Process Disruption
Malicious or malformed firmware can degrade performance, trigger watchdog resets, or render equipment inoperable. In tightly coupled environments, even milliseconds of downtime may halt production lines, induce mechanical stress, or break synchronization. Ransomware targeting embedded devices is especially damaging because many systems lack rapid recovery paths.
![]() Compromised Update Infrastructure
Compromised Update Infrastructure
Update servers, remote support portals, and vendor diagnostic tools have become high‑value targets. If attackers infiltrate these components, they can distribute weaponized updates at scale, effectively turning the vendor’s supply chain into an attack vector. These channels are particularly dangerous because operators often trust vendor‑signed updates without additional verification.
![]() Manipulated Configuration or Safety Limits
Manipulated Configuration or Safety Limits
OT devices often store pressure caps, temperature ceilings, torque limits, and other safety thresholds in firmware or configuration memory. Weak access controls allow adversaries to subtly modify these values without immediate operational disruption. Such manipulations may remain dormant forlong periods and only manifest under specific operating conditions.
Standards such as NIST SP 800‑82r3 and IEC 62443‑4‑1/4‑2 now explicitly require secure development, update, and supply chain practices for OT components.
A Technical Analysis¶
OT Assets Now Depend on Embedded Operating Systems
Industrial controllers, HMIs, gateways, and sensors commonly run:
-
Yocto or Debian‑based Linux
-
Android or AOSP derivatives
-
Custom bootloaders (U‑Boot, Barebox, LK/ABL)
-
Vendor BSPs with kernel modifications
Weaknesses at any of these layers directly compromise OT reliability.
Remote Updates Increase Exposure
NIST SP 800‑82 emphasizes that remote update channels must enforce:
-
Cryptographic authenticity
-
Integrity verification
-
Rollback protection
-
Resilience against partial or failed updates
Poorly designed OTA mechanisms are now among the most impactful OT attack vectors.
Software Supply Chain Integrity Is Mandatory
IEC 62443‑4‑1 and 4‑2 require:
-
Verified components at build time
-
Secure code provenance
-
Trusted CI/CD pipelines
-
Repeatable, traceable builds
Compromised firmware images can propagate vulnerabilities deep into industrial systems.
Embedded Devices Often Lack Lifecycle Maintenance
OT deployments often operate for 10–20 years. Their security posture degrades unless update mechanisms:
-
Remain functional across hardware generations
-
Provide reproducible builds
-
Support secure recovery paths
-
Validate software origin even decades later
Lifecycle support is now a core embedded security requirement.
How Kynetics Addresses These Key Security Gaps¶
Kynetics operates in alignment with NIST and IEC 62443 requirements for embedded OT systems.
Secure and Verified Update Delivery¶
Update Factory OTA offers:
-
Cryptographically signed packages
-
Atomic, fail‑safe system updates
-
A/B partitioning
-
Custom update pipelines for Linux and Android
-
Offline and staged deployments for OT environments
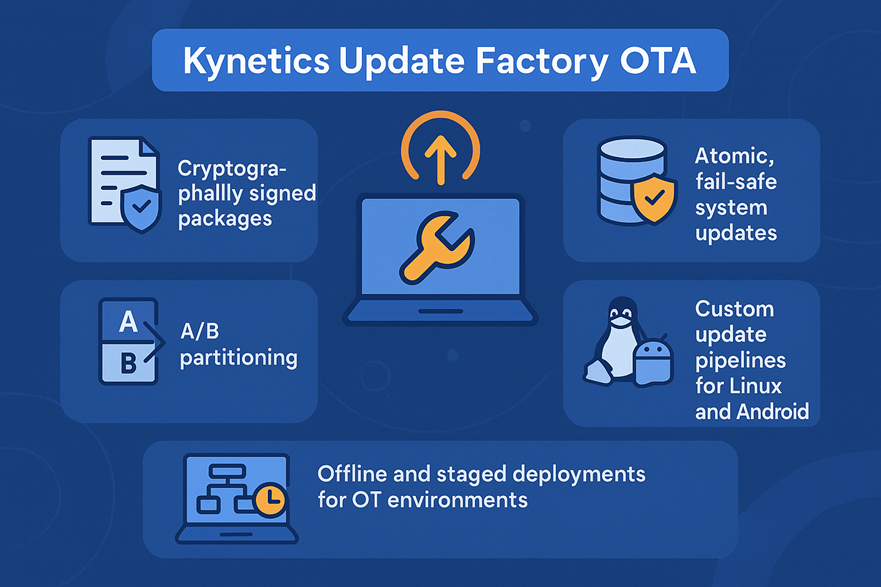
These capabilities meet the update authenticity and rollback prevention requirements in NIST SP 800‑82 and IEC 62443‑4‑2.
Trusted Boot Chains and Firmware Verification
Kynetics bootloader engineering provides:
-
U‑Boot secure boot enablement
-
Android Verified Boot (AVB) v2
-
Custom chain‑of‑trust designs
-
TPM integration and key management
These features enforce firmware integrity at boot, critical for devices vulnerable to physical or network tampering.
Reproducible and Traceable BSP Management
Kynetics supports BSP maintenance for:
-
Yocto‑based systems
-
Android BSPs and HAL layers
-
Board bring‑up and long‑term OS maintenance
This ensures repeatable builds, long‑term support, and compliance with IEC 62443 lifecycle requirements, reducing the supply-chain risk.
Final Recommendations
-
Adopt a secure boot chain for all OT Linux/Android devices.
-
Implement verified OTA mechanisms with atomicity and rollback protection.
-
Harden build systems with reproducible builds and artifact signing.
-
Maintain long‑term OS/BSP support, especially for Linux kernels and Android frameworks.
-
Integrate supply chain risk management consistent with IEC 62443 and NIST SP 800‑82.
-
Perform periodic firmware integrity checks on deployed OT assets.
Reach out to our team at Kynetics if you need help securing your OT devices.
References and further reading¶
NIST SP 800-82 Guide to Operational Technology (OT) Security https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-82r3.pdf
IEC 62443 Series Industrial Automation and Control Systems Security https://www.isa.org/standards-and-publications/isa-standards/isa-iec-62443-series-of-standards
OWASP Embedded Application Security Project https://owasp.org/www-project-embedded-application-security/
Dragos – OT & Industrial Cybersecurity Research https://www.dragos.com/